[Homelab] Build your own Vulnlab with Docker
Vulnlab Installation
Installation Docker + Portainer
Welcome! After a short break I created my own open source Vulnlab. It is hosted on a Docker Container on a Raspberry Pi 5.
With Docker I can get very fast an Application which I can host in my network for penetration testing.
Below a very short Installation Guide for installing Docker on a Linux Device (in my case a Raspberry Pi) with Portainer:
- We download the Docker script from Docker
curl -fsSL https://get.Docker.com -o get-Docker.sh - Execute the script
sudo sh get-Docker.sh - Add the current user to the group
docker:sudo usermod -aG docker $USER - This applies the new group membership without requiring a full logout.
newgrp docker This pulls and runs the official hello-world Docker image:
docker run hello-worldCreates a persistent volume named portainer_data. Volumes are used to store persistent data outside of containers.
docker volume create portainer_data- This runs and gets the container
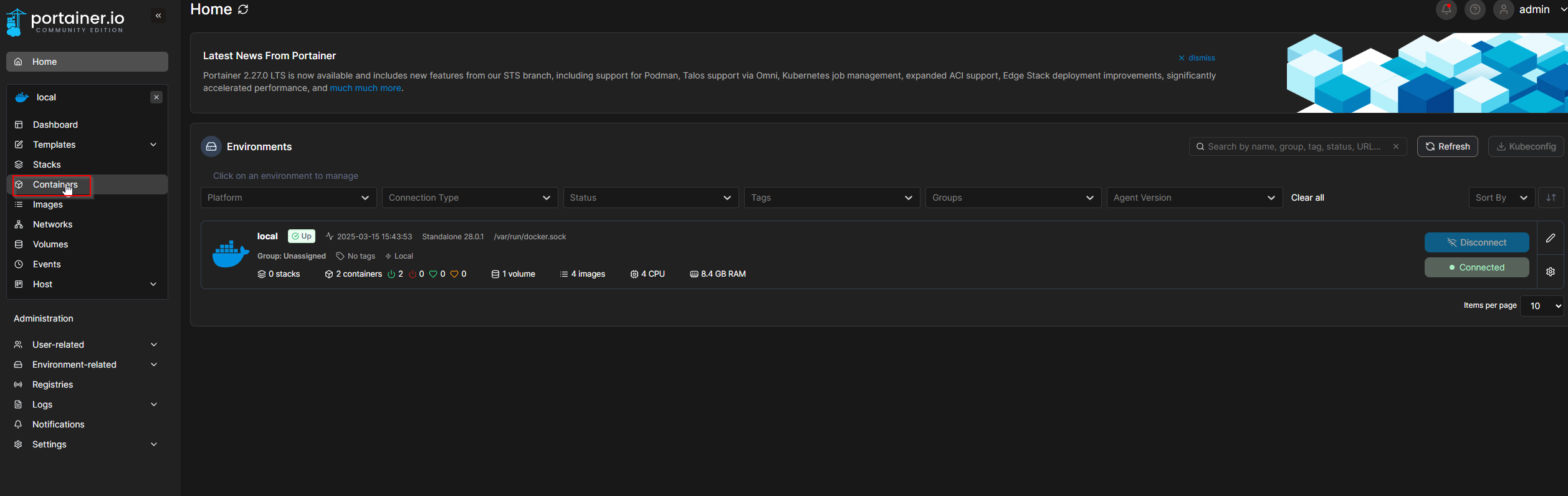
Portaineron Port9443.
1
docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latest
- Login on
127.0.0.1:9443.
It should look like that:
Installation Vulnlab from Yavuzlar
Now that we have docker running, we can easily install and manage our apps with it and portainer in a GUI.
For the installation we do the following:
Manual Installation
- Clone the repo
git clone https://github.com/Yavuzlar/VulnLab - Build docker image
docker build -t yavuzlar/vulnlab . - Run container
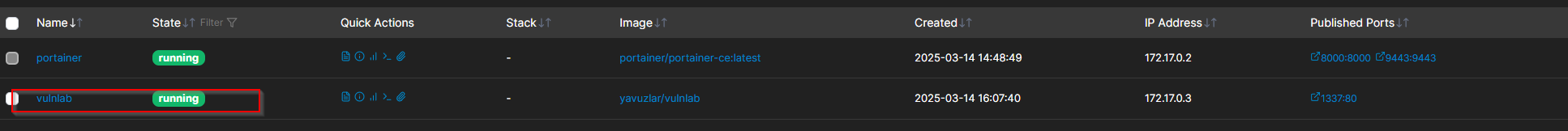
docker run -d -p 1337:80 yavuzlar/vulnlab
Now we should see the container in Portainer and reach it on port 1337:
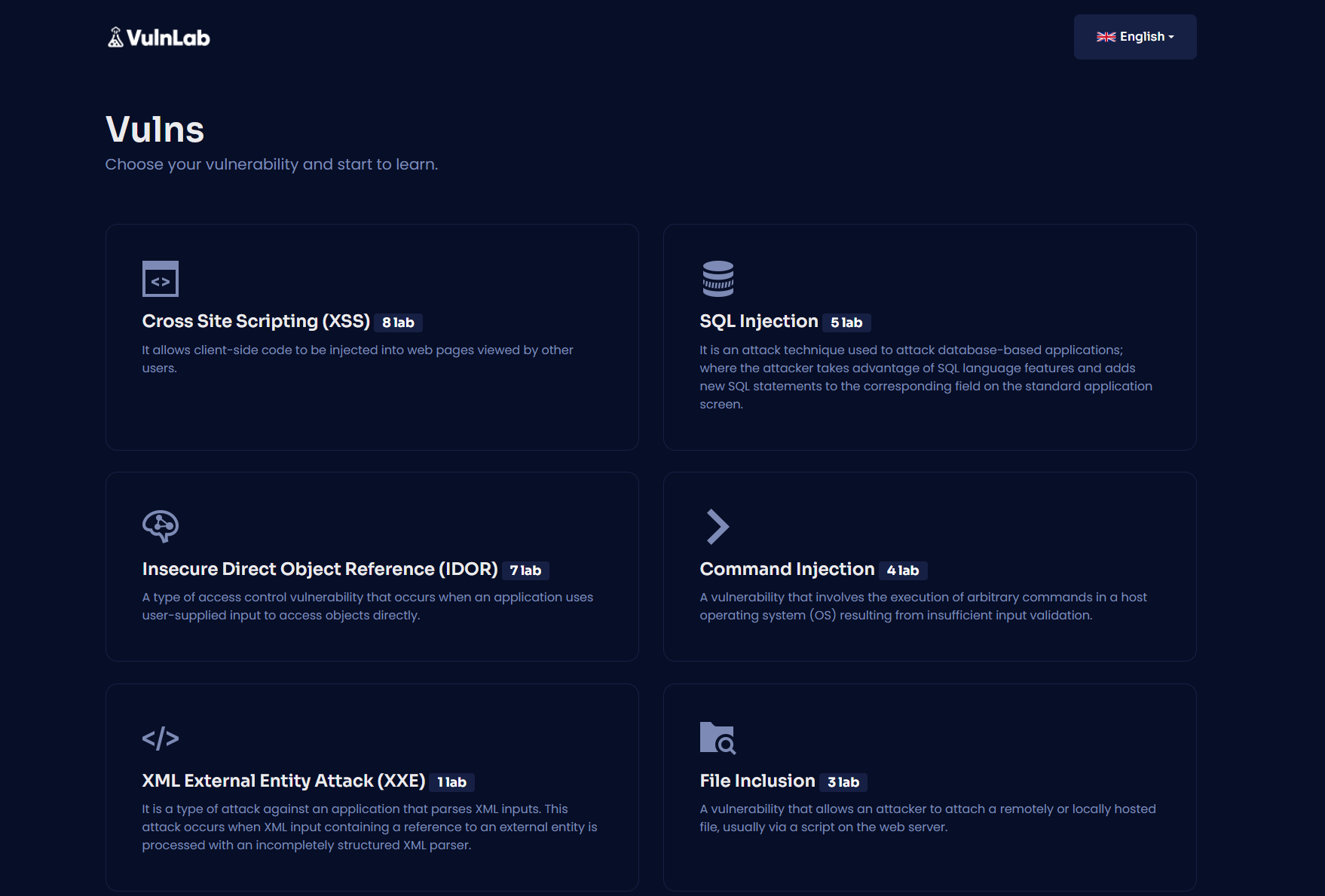
The application looks like that:
Hope you found this guide useful. Now we can try all of our red team techniques on our own hosted app.